MAC address whitelisting is commonly perceived as a foolproof network security mechanism. Yet, Brackish Security’s recent test on a wireless network illustrates how easily this method can be bypassed, challenging its efficacy as a standalone security solution.
MAC address whitelisting operates on the premise that only devices with pre-approved MAC addresses can access a network. This method is based on the unique hardware address of network devices, seemingly offering a straightforward approach to secure network access.
During a recent wireless engagement, we deployed one of our drop boxes, a small form factor computer to assess the network. The organization was a medium sized business that utilized a pre-shared key wireless network.
Included with our drop box was a cellular card that allowed us to access the machine remotely. We were quickly able to obtain the four-way handshake for the wireless network, create a custom wordlist and crack the wireless password hash (but that’s not what this blog is about!).
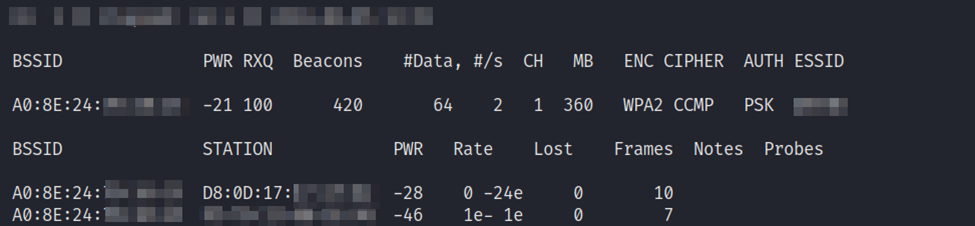
Upon authenticating into the network, to our surprise, we had no access… Our attempts to access resources internally and externally were getting blocked and redirected. Okay well that to do now? Well, perhaps they have implemented MAC address whitelisting. Okay, back to airodump-ng.
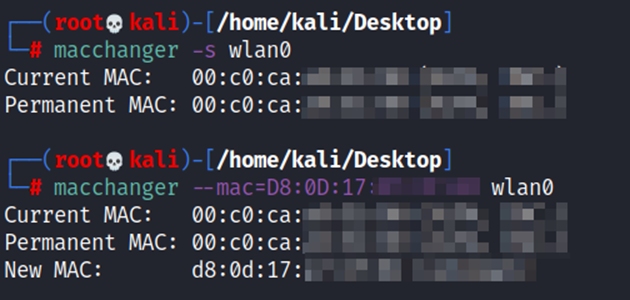
Placing the wireless card back into monitor mode, we quickly grabbed a MAC address of a connected device. Using a tool built-in to Kali, ‘macchanger’, in two commands we changed our MAC address to the currently connected device. Viola! (Disclaimer: Screenshots are from a lab environment)
Why MAC Address Whitelisting Falls Short: The engagement highlights two critical vulnerabilities in MAC address whitelisting:
- MAC Addresses Are Public: Since MAC addresses are transmitted openly over networks, they are easily discoverable by anyone with basic sniffing tools.
- Spoofing Simplicity: Changing a device’s MAC address to mimic another is relatively straightforward, using readily available software.
The Illusion of Security: Relying solely on MAC address whitelisting can create a false sense of security. It’s a static, easily circumvented measure that can be exploited by even moderately skilled attackers.
Recommendations: For a more robust defense, Brackish Security recommends:
- Layered Security Approach: Combine MAC address whitelisting with dynamic security measures like WPA2 Enterprise, which offers more stringent authentication.
- Regular Network Monitoring: Implement continuous monitoring to detect and respond to suspicious activities, including MAC spoofing attempts.
- Frequent Security Audits: Regularly update and review network security protocols to address new and evolving threats.
Brackish Security’s findings serve as a crucial reminder that in the realm of cybersecurity, static defenses like MAC address whitelisting are inadequate on their own. A multi-faceted, dynamic approach is essential for effective network security in today’s ever-evolving threat landscape.




