TutorTrac Multiple Stored XSS
Brackish researchers found authenticated stored cross-site-scripting (XSS) in TutorTrac version <= 4.2.170210. An authenticated attacker could utilize crafted input in several locations throughout the application to perform XSS attacks. This is a standard stored XSS attack that can be used to steal user’s sessions cookies, amongst other things.
Injection is a current OWASP Top Ten vulnerability, and although we see less of these as the years go by, XSS still remains prevalent – even in modern applications.
Where?
The first locations are reason and location fields of the visits listing page. It appears as if input filtering is performed somewhat well, but the img tag seems to have been ignored.
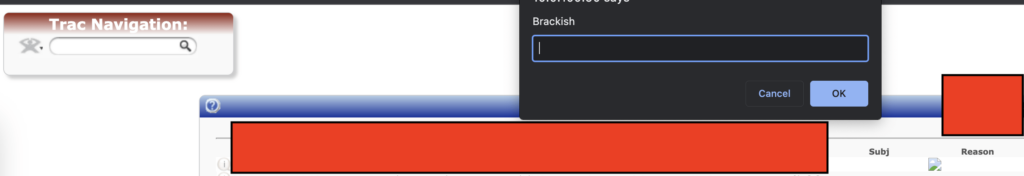
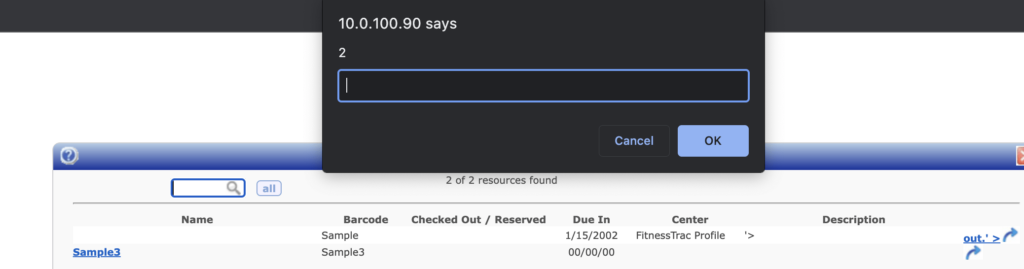
Other locations are also susceptible to the same XSS payloads. For example, several potential assignments section fields and resources listings > title and description fields.
How to fix?
At the root of injection vulnerabilities is user input sanitization and validation. Depending on the programming language and framework(s) used, functions are provided to to perform these functions. It is recommended to use these functions and not ‘roll your own’ routines.
Additionally, it is imperative that code reviews and penetration tests are done all on applications. If you or your company needs help, please reach out to Brackish!



