With 2025 in the bag, we wanted to start an annual series highlighting the top findings from the previous year. As trends and technology shifts, as will these findings. We will start with external and dive into internal & web app from here.
External network penetration testing evaluates how an organization appears to an attacker on the internet with no credentials, no internal access, and no prior knowledge. Probably the most important test when shopping for penetration testing services.
While perimeter defenses continue to improve, our testing throughout 2025 shows that many organizations remain exposed through a small set of repeatable weaknesses.
Exposed Management and Administrative Interfaces
One of the most consistent findings in external assessments is the exposure of management interfaces to the public internet.
These commonly include:
- Firewall, router, and load balancer administrative portals
- VPN management interfaces
- Remote access gateways and infrastructure management tools
In many cases, these services were deployed for convenience or temporary access and never properly restricted or removed.
Administrative interfaces are high-value targets. Even when patched, their exposure increases the risk of credential attacks, brute-force attempts, and exploitation of future vulnerabilities.
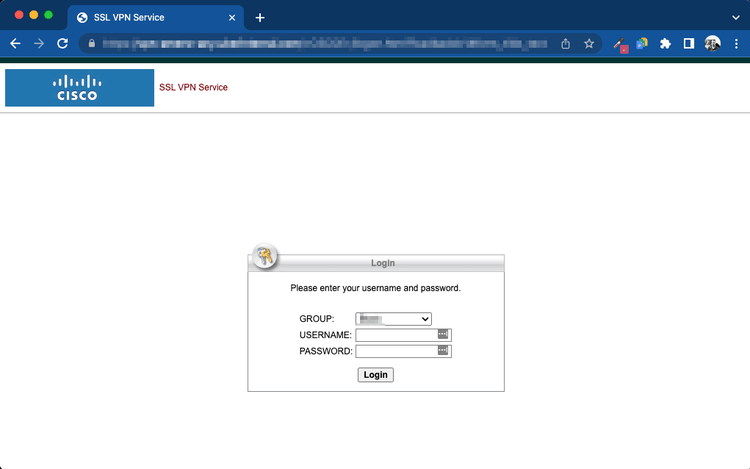
Weak or Incomplete Authentication Controls
Multi-factor authentication adoption has increased, but gaps remain, especially on legacy or secondary systems.
We frequently observe:
- Internet facing services protected only by username and password
- MFA enabled for some users but not enforced universally
- Legacy VPNs or portals that do not support modern authentication standards
Attackers rarely need to exploit software flaws when valid credentials can be obtained through password spraying or reused from prior breaches.
Credential-based attacks are simple, difficult to detect, and highly effective against externally exposed services.
Credential Stuffing
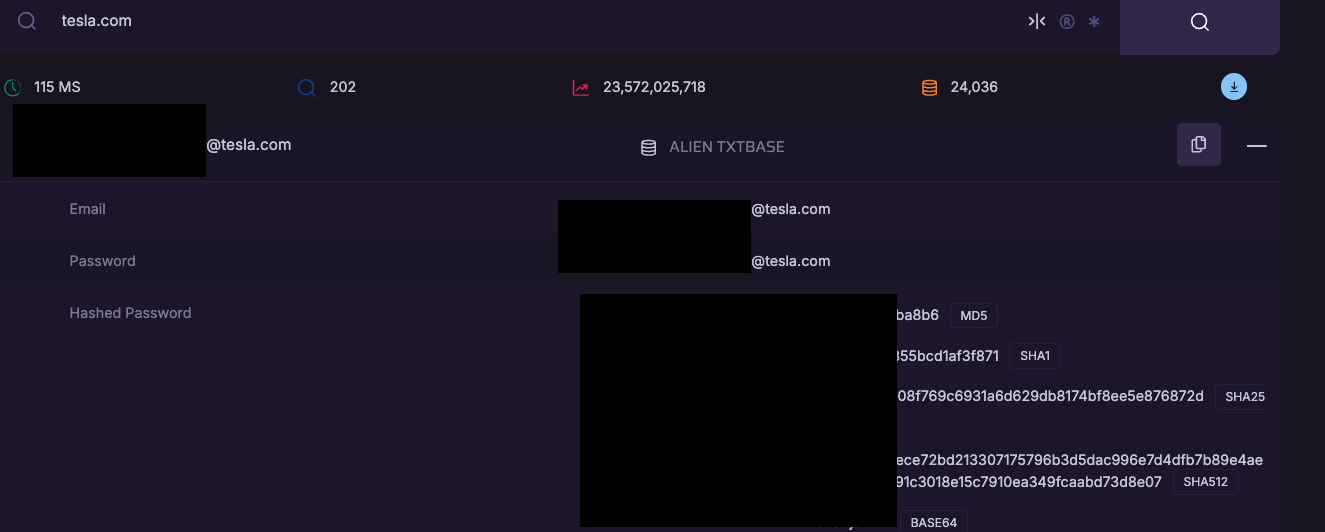
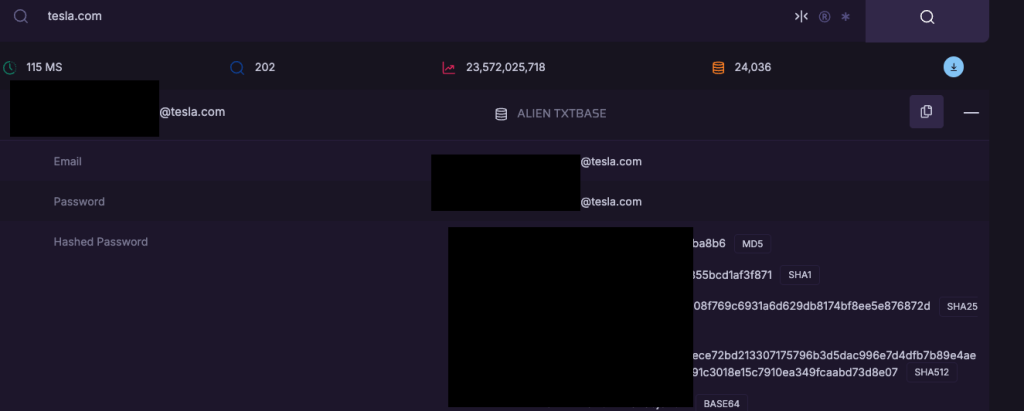
When email addresses or usernames are known, attackers attempt direct authentication using passwords from historical breach datasets. On our externals, we use dehashed.com breach data to identify compromised employee username and password information. Typically, not very fruitful, but it’s not uncommon for some level of success that is met with an MFA prompt. The successful attempts can be utilized later on the internal. We’ve noticed a fair number of success in 2025.
Common targets for credential stuffing:
- VPN Portals
- Web App Portals
- Outlook Web Access (OWA)
Unnecessary External Service Exposure
Organizations often expose more services to the internet than required for business operations.
Examples include:
- Legacy web applications no longer actively maintained
- Alternate ports exposing duplicate services
- Debug or administrative endpoints left accessible
These services frequently fall outside standard patching and monitoring processes.
Every exposed service expands the attack surface and increases the likelihood of compromise through overlooked vulnerabilities.
Outdated or End-of-Life External Systems
End-of-life systems remain a recurring external finding in 2025.
These systems often:
- No longer receive security updates
- Use outdated encryption or protocols
- Cannot be properly monitored or hardened
While they may be considered “low risk” due to limited usage, attackers actively target these systems because they are predictable and reliable.
EOL systems provide stable entry points that attackers can exploit repeatedly with minimal effort.