Welcome to the first of many parts of our series on Mobile Application Penetration Testing. We wanted to write this series because it seems like a lot of the material out there on mobile application penetration testing is out of date, wrong, or lacking. Furthermore, when it comes to mobile application penetration testing, there are many ways to accomplish the same thing, which can lead to confusion.
And for those of you that are bug bounty hunters, mobile apps tend to get looked at less than standard web apps, so maybe this is something you should consider. Something else to consider is that mobile applications are often intertwined with Internet of Things (IoT) devices, which can lead to all sorts of novel and impactful vulnerabilities.
Jailbreaking and Rooting
While we’d like to offer you an in-depth guide on jailbreaking iOS and rooting Android devices, the process can be complex and device-specific. Moreover, much of the information available online is outdated or not universally applicable. Instead of providing explicit instructions here, we’ll direct you to reliable sources where you can explore your options depending on your phone and OS version. Be prepared to invest some time in research.
iOS
- https://www.reddit.com/r/jailbreak – Just ask questions here or look for information. Generally you can get the most up to date advice here.
- https://ios.cfw.guide/ – This site has information on the latest jailbreaks for your iOS devices.
Android
- https://www.blackhillsinfosec.com/start-to-finish-configuring-an-android-phone-for-pentesting/ – This will walk you through rooting an Android phone. I’ve followed this article about a year ago and successfully rooted an Android device.
- https://www.reddit.com/r/Android – As above for iOS, ask your questions here.
As pentesters and bug bounty hunters, you’ll generally need to have a rooted/jailbroken device in order to bypass certificate pinning, which will allow you to intercept HTTPS requests in Burp as you would for a normal web application.
Certificate pinning is a security measure employed in mobile applications to enhance the protection of HTTPS communications. Normally, when a mobile app communicates with a server over HTTPS, the server presents a certificate which the client validates against a list of trusted Certificate Authorities (CAs). However, this approach is vulnerable to attacks like Man-in-the-Middle (MitM) if a CA is compromised, rogue certificates are issued, or the validation process is otherwise subverted.
In certificate pinning, the mobile app has a copy or ‘fingerprint’ of the expected server certificate or public key embedded within it. When the app establishes a connection, it validates the server’s certificate against this pre-stored information rather than relying solely on the OS or browser’s list of trusted CAs. If the certificates do not match, the app can terminate the connection, thus averting potential MitM attacks.
Again, if you’re a pentester, you may be able to have the client supply an application without protections like certificate pinning or even jailbreak/root detection, but bug bounty hunters may need to deal with both.
But while you’re trying to jailbreak or root your device, we can get started with some other aspects of mobile penetration testing.
Getting an IPA (not a beer) and APK
What are IPAs and APKs, you may ask?
- IPA (iOS App Store Package): This is the extension for iOS applications. An IPA file is an archive file that stores an iPhone, iPad, or iPod Touch app. It contains all the resources needed for the app to function—code, assets, frameworks, etc. Essentially, it’s a compiled and packaged version of the app ready for deployment on iOS devices. The IPA files are encrypted and can be decrypted and installed only by Apple-issued certificates.
- APK (Android Package): APK files are analogous to IPA files, but for the Android ecosystem. An APK is an archive file containing the compiled Android application code, resources, and manifest. It’s used to distribute and install applications on Android devices. Unlike iOS, Android allows for easier sideloading of APKs, although this comes with its own security risks.
There are many ways to obtain these files, including multiple gray legality sites out there that let you download them. Google search those on your own time. Here we will show you easy ways to obtain these without downloading them from sites of ill repute.
IPA
On iOS, we are going to get the IPA with the ipatool application. You’ll also need Homebrew installed on your Mac. Once Homebrew is installed, run the following command to install ipatool.
brew install ipatool
Once installed, you’ll need to authenticate to the app store with the following command (use your email address not example.com):
ipatool auth login -e [email protected]
follow the prompts and authenticate. Once authenticated, we can search for the app we want. Today we will use YouTube.

Once we get the bundleID, com.google.ios.youtube, we can download the IPA:
ipatool download --bundle-identifier com.google.ios.youtube --output ./youtube.ipa
Tada! You now have an IPA. Keep in mind that this is only one way of obtaining an IPA. There are many other ways out there, and a simple Google search will find them.
APK
To get the APK, we are going to install Android Debug Bridge (ADB) via the methods found at this link
https://www.xda-developers.com/install-adb-windows-macos-linux/
Installation will vary depending on your operating system. ADB is a very useful tool that is required for Android penetration testing. Despite there being other ways to obtain an APK, we need to install ADB, so we may as well use ADB to get an APK.
Once installed, use the following command to list Android packages.
adb shell pm list packages
Which will give you a long output of packages. Here is mine cropped down a lot.
If you inspect the output, you’ll find the YouTube application.
package:com.google.android.youtube
Now, let’s get the APK with these commands to get the app path, then download the APK.
adb shell pm path com.google.android.youtube
then
adb pull /data/app/~~GrnX299b-71WZa2U6OIc_A==/com.google.android.youtube-r475Mya4fW1lt0NlLjHY1A==/base.apk ~/Downloads/youtube.apk
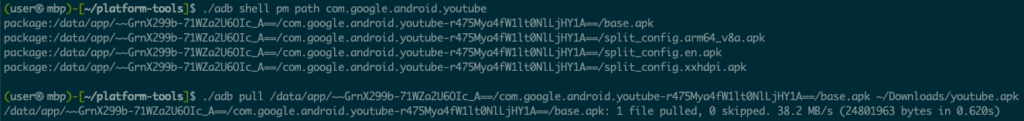
And now we have the APK for analysis.
More Coming Soon in Our Mobile Application Penetration Testing Series
While this is the end of Part One, stay tuned for more in our mobile application penetration testing series where we will discuss MobSF, Frida, Objection, Android specific testings, iOS specific testing, and much, much more.
Update: Part 2 here!
