As penetration testers, like SharePoint, (check out our previous blog post here https://brackish.io/the-risks-of-storing-passwords-in-sharepoint), Bitbucket is a gold mine for credentials. In the dynamic world of software development, tools like Bitbucket are indispensable for version control and collaboration. However, a common yet often overlooked security misstep is the storage of sensitive information, such as passwords, within these repositories. This blog post aims to shed light on the security risks associated with storing passwords in Bitbucket and offers practical recommendations for remediation.’), Bitbucket is a gold mine for credentials. In the dynamic world of software development, tools like Bitbucket are indispensable for version control and collaboration. However, a common yet often overlooked security misstep is the storage of sensitive information, such as passwords, within these repositories. This blog post aims to shed light on the security risks associated with storing passwords in Bitbucket and offers practical recommendations for remediation.
The Risks of Storing Passwords in Bitbucket
Accidental Exposure
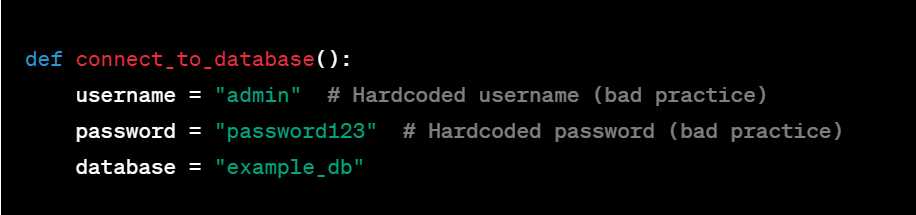
One of the primary risks of storing passwords in Bitbucket, or any version control system, is accidental exposure. Developers might inadvertently commit files containing credentials, making them accessible to anyone with access to the repository, and potentially even to the public if the repository isn’t private.
Target for Cyber Attacks
Repositories storing sensitive data like passwords become prime targets for cyber attackers. With access to these credentials, attackers can potentially gain unauthorized access to other parts of the system, leading to data breaches or more severe security incidents.
Non-Compliance Issues
Storing passwords in plain text or in an unsecured manner can lead to non-compliance with various data protection regulations like GDPR, HIPAA, etc., potentially resulting in legal ramifications and fines.
Best Practices for Remediation
Regular Scans for Sensitive Data
- Implement tools that scan repositories for sensitive information and alert the team when such data is found. This proactive approach can prevent passwords from lingering in your Bitbucket repositories unnoticed.
Educate and Implement Policies
- Conduct training sessions for development teams on the importance of safeguarding sensitive data.
- Establish clear policies regarding what can and cannot be stored in version control systems.
Use Environment Variables
- Store sensitive data like passwords in environment variables instead of hardcoding them into your codebase. This practice keeps credentials separate from code and minimizes the risk of accidental exposure.
Implement Secret Management Tools
- Utilize secret management tools like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault. These tools are designed to securely store, access, and manage sensitive data like API keys, passwords, and certificates.
Enforce Code Reviews
- Regular code reviews can be an effective line of defense against committing sensitive information. Ensure that all code is reviewed by at least one other team member before merging.
Immediate Revocation and Rotation of Exposed Credentials
- If a password or other sensitive data is found in Bitbucket, immediately revoke the exposed credentials and rotate them to new ones. This limits the window of opportunity for any potential misuse.
Gitignore and Clean History
- Use
.gitignorefiles to prevent specific files or folders containing sensitive information from being committed. - If passwords are found in the repository’s history, use tools like BFG Repo-Cleaner or git filter-branch to clean your commit history.
The storage of passwords in Bitbucket is a critical security concern that can lead to significant risks. By employing rigorous scanning, education, secret management tools, and strict code review policies, businesses can mitigate these risks and maintain a robust security posture. Remember, vigilance and proactive measures are key to safeguarding your digital assets in the evolving landscape of cybersecurity.