We wanted to create this blog series to highlight how important regular penetration testing is and how it effectively reduces risk. This week we will focus on port 3389, traditionally used for Windows Remote Desktop Protocol (RDP), which allows users to access their desktop over a network connection. It’s like leaving the keys in the lock of your front door. Today, we dive into recent findings from Shodan, the “search engine for Internet-connected devices,” which show an alarming number of port 3389 exposures across the globe.
What Is Shodan?
Shodan is at this point, a well-known service that scans the internet, looking for IP addresses with open ports that signify active services like web servers, databases, and other devices connected to the internet. Think of it as a map of digital doors and windows, some locked and others wide open. Security teams and hackers alike can use Shodan to discover devices open to the internet, making it a double-edged sword.
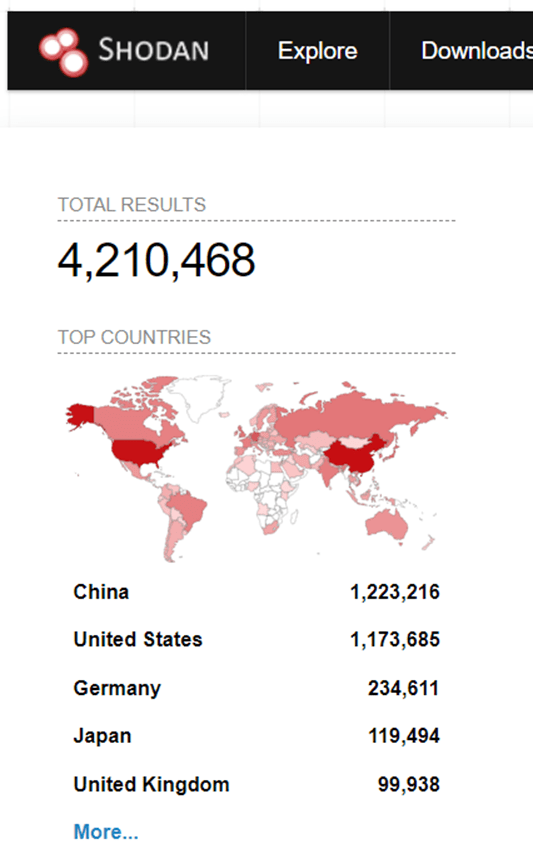
A simple search for port 3389 (RDP) into Shodan reveals a staggering number of devices exposed, Figure 1. These devices are predominantly Windows servers, but are occasionally other items, such as a Raspberry Pis and devices that need remote connectivity.
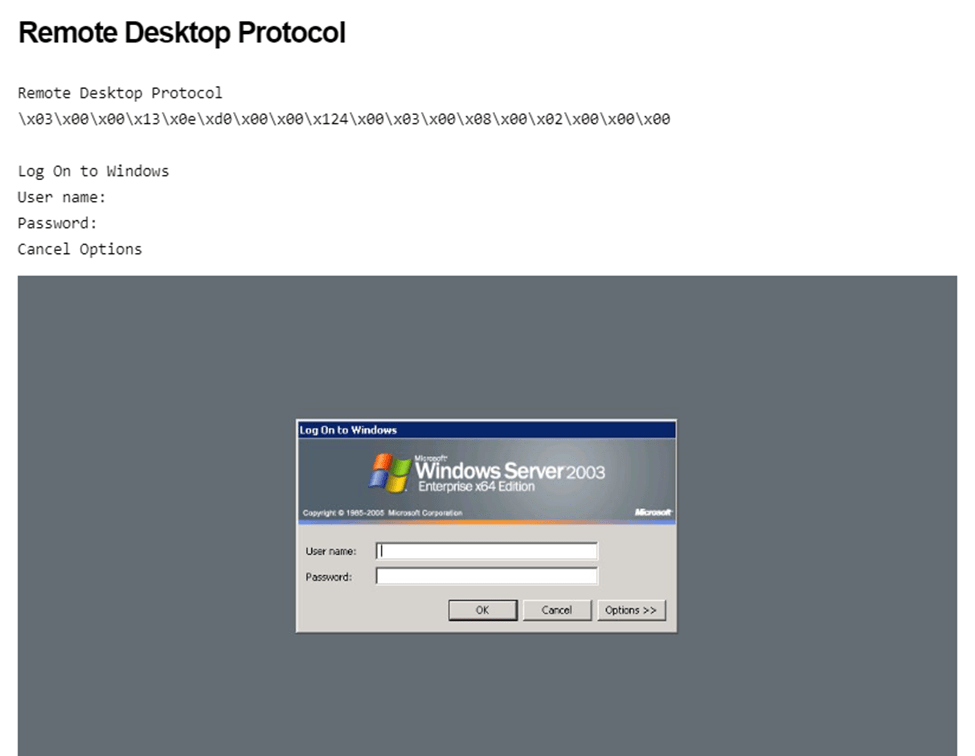
Shodan will take screenshots of devices it connects to, Figure 2 displays a deprecated version of Windows Server 2003 that reached end of life in 2015 with several known high severity vulnerabilities.
So why did we decide to focus on RDP?
Remote Access as a Target: Port 3389 is used by RDP, a valuable target for attackers since it provides direct access to a user’s desktop environment.
Brute Force Attacks: With RDP exposed, attackers can attempt brute force attacks, where they try various password combinations to gain access.
Proliferation of Ransomware: RDP vulnerabilities have been linked to ransomware attacks, where attackers encrypt files on the network and demand a ransom to unlock them.
RDP shares a glimpse into your organizations network, architecture and can even enumerate username information.
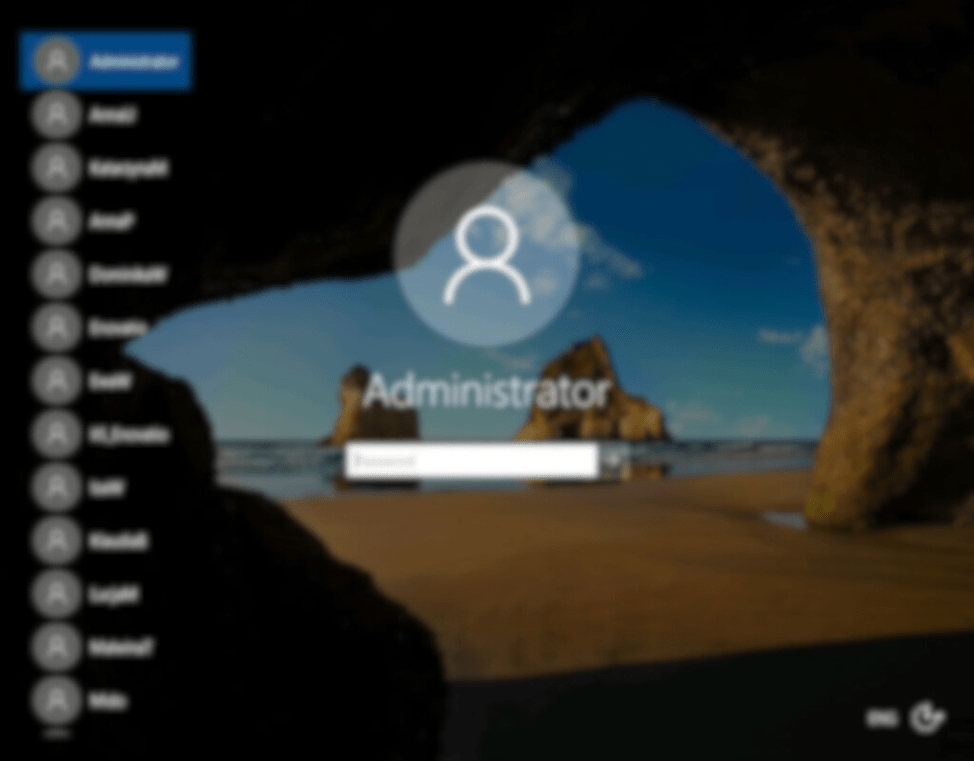
Figure 3 is a familiar screen to most, it’s a login screen to a Windows desktop. In this case, it’s exposed publicly to the internet and on the left side of screen provides attackers names of users that have logged in previously. This information can be used in an attempt to login directly to this server or provide an attacker some open-source intelligence on a target organization to mount a more sophisticated attack.
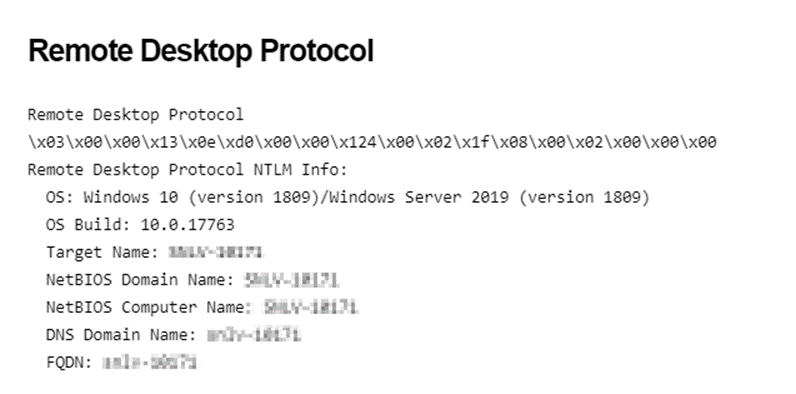
Shodan banner grabs server information, stores it and returns it. Figure 4 displays server version and hostname information (obfuscated). Knowing a hostname helps an attacker map the network’s structure. It can reveal the naming convention used within the network, which often includes clues about the role, location, or operating system of a device. Versioning data can provide an attacker insight into the patching cycle to make assumptions about security controls and vulnerabilities specific to the version.
When port 3389 is exposed to the internet, it’s an open invitation to cybercriminals. The risks range from unauthorized access and control of the network to the potential theft of sensitive data. This exposure becomes a gateway for various nefarious activities:
Data Theft: Attackers can steal company or personal data, leading to financial loss and identity theft.
Spyware: Unfettered access could allow for the installation of spyware to monitor keystrokes and other activities.
Network Disruption: Hackers could disrupt operations, leading to downtime and loss of business.
Resource Hijacking: Attackers might use the compromised system to launch further attacks, masking their true location and identity.
So what can you do as a business?
Implement a VPN: Require all RDP sessions to be conducted through a Virtual Private Network (VPN). This ensures that RDP is not directly exposed to the internet and adds a layer of encryption.
Disable RDP: If RDP is not required, it’s safest to disable it entirely.
Consider Alternative Solutions: If possible, consider using more secure remote access solutions that offer better security features than RDP.
Regularly scheduled penetration tests will quickly identify any devices that may have RDP enabled or had recently been enabled. Contact us to get your next test scheduled! [email protected]



