Our goal of this series is to revisit Shodan and demonstrate to IT admins and business owners, how much an attacker can glean of a network without sending any packets to the actual to an organization. Our last post focused on Remote Desktop Protocol being exposed to the publicly accessible internet: https://brackish.io/shodan-series-part-1-the-accidental-open-door/
This week we want to look at one of our personal favorites, webservers on untraditional ports. Traditional ports being 80 & 443. There are plenty of reasons why ports deviate from their industry standard, but often introduce additional security risks to an organization.
Lets take a look at how many webservers in the United States have port 8080 exposed. Figure 1 displays 2.5 million! Yeah, some of them are behind Cloudflare and some may be honeypots. But this is just a start
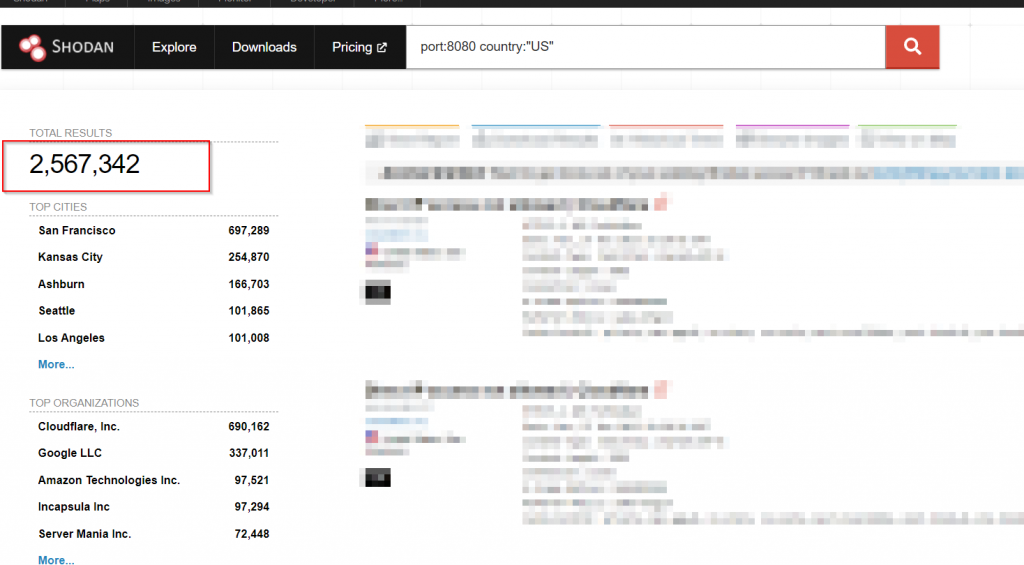
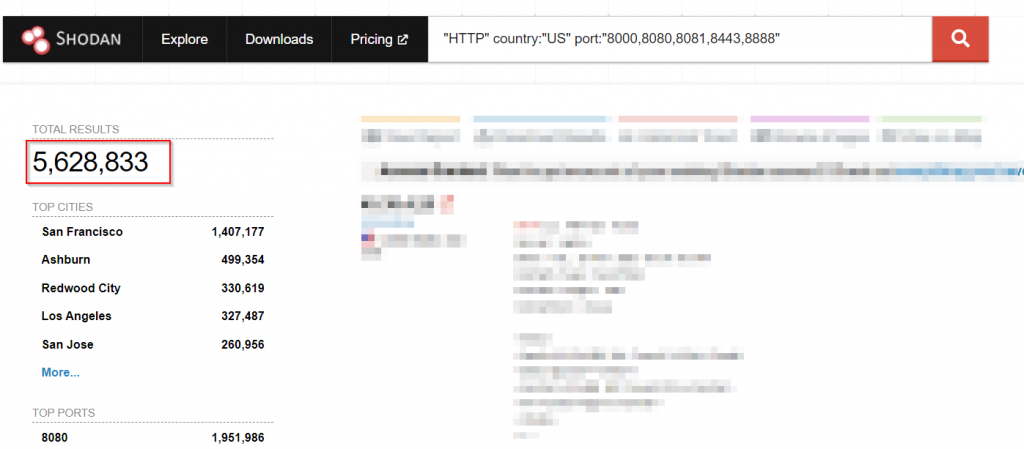
A more detailed search including HTTP headers in the server response to remove services outside of webservers.
Manually browsing some of the web pages can be eye-opening: Here is a response from a roadway sign alerting citizens of snow plows. This application may have default credentials or known vulnerabilities allowing an attacker to alter the sign or cause a disruption.

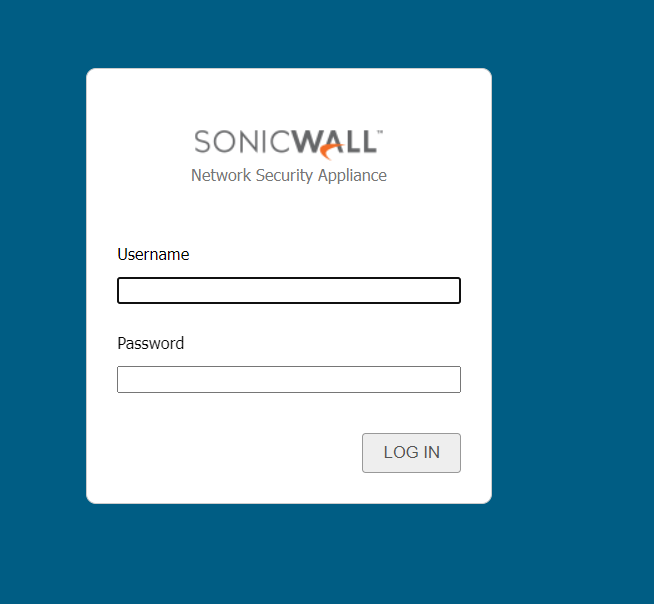
Oftentimes, higher ports are used for admins to authenticate into the front end of the application to modify the application.
Login to a sonicwall firewall exposed on port 8080.
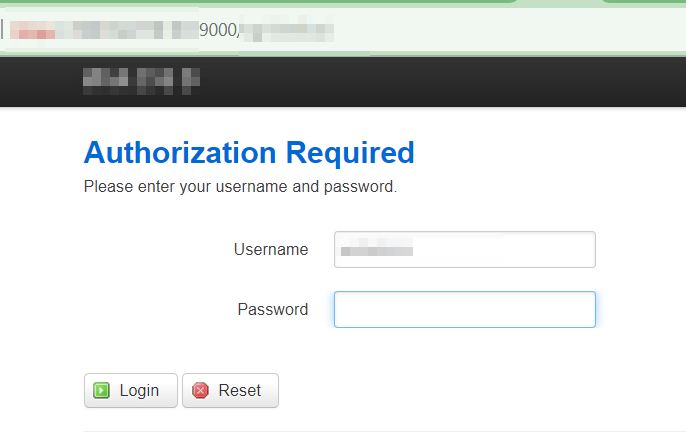
Here is an admin page with a pre-populated username.
You might be asking: Why Do Organizations Deviate from Standard Ports?
- Avoiding Port Conflicts: In environments where multiple web servers run on a single machine, alternative ports like 8080 or 8000 are used to prevent conflicts.
- Security Through Obscurity: Some believe that using non-standard ports (like 8443, 8081, or 8008) can reduce exposure to automated attacks that commonly target ports 80 and 443.
- Development and Testing: Non-traditional ports are often used for development and testing purposes. Developers use ports like 3000 (common in Node.js) or 8080 to avoid requiring elevated permissions needed for ports below 1024.
- Bypassing Firewalls and Filters: Certain networks restrict traffic on standard web ports. Using alternative ports can be a workaround to these restrictions.
Risks of Exposed Non-Traditional Ports on Shodan
- Admin Panels: Often times a website or device may utilize a higher port as the administrator interface.
- Security Misconception: Relying solely on obscurity is a flawed security practice. While non-standard ports might evade some automated scans, they are not immune to targeted attacks.
- Increased Attack Surface: Exposing additional ports increases the attack surface. Each open port is a potential entry point for an attacker.
- Compliance Issues: Operating on non-standard ports can raise compliance issues, especially where specific port use is mandated for regulated data.
- Overlooked in Security Policies: These ports can be overlooked in security monitoring and policies, making them vulnerable to exploits.
Best Practices for Managing Non-Traditional Ports
- Regular Vulnerability Scanning: Use tools to scan for exposed ports. Regular scans help identify and mitigate risks associated with open ports.
- Robust Security Measures: Implement stringent security measures, including firewalls, intrusion detection systems, and rigorous access controls, regardless of the port being used.
- Closing Unnecessary Ports: If a non-traditional port is not in active use, it should be closed to prevent unauthorized access.
- Monitoring and Logging: Keep detailed logs of traffic to non-traditional ports and monitor them for unusual activities.
- Educate and Train Staff: Ensure that your team is aware of the risks associated with using and exposing non-standard ports.
While there are legitimate reasons for web servers to operate on non-traditional ports, their exposure to the internet should be managed with caution. At Brackish Security, we emphasize the importance of not relying on obscurity for security. Proper configuration, regular security assessments, and adher
